In a Zerologon exploit, an attacker with access to a network takes advantage of a critical flaw in the Netlogon Remote Protocol (MS-NRPC) to impersonate any computer, including a domain controller (DC). This flaw is known as Zerologon—a vulnerability that can give attackers full control over a domain.
What is a Zerologon exploit?
Attackers that successfully exploit the Zerologon vulnerability, also known as CVE-2020-1472, typically send specially crafted Netlogon authentication requests that bypass cryptographic checks. The attackers are thus able to change the password of the DC’s computer account, effectively giving them full control over the domain. No authentication or elevated privileges are needed to launch the attack.
Figure 1 shows the help command output for a Zerologon exploit in Cobalt Strike. This output explains how to use the Zerologon vulnerability to reset the machine account password of a DC.
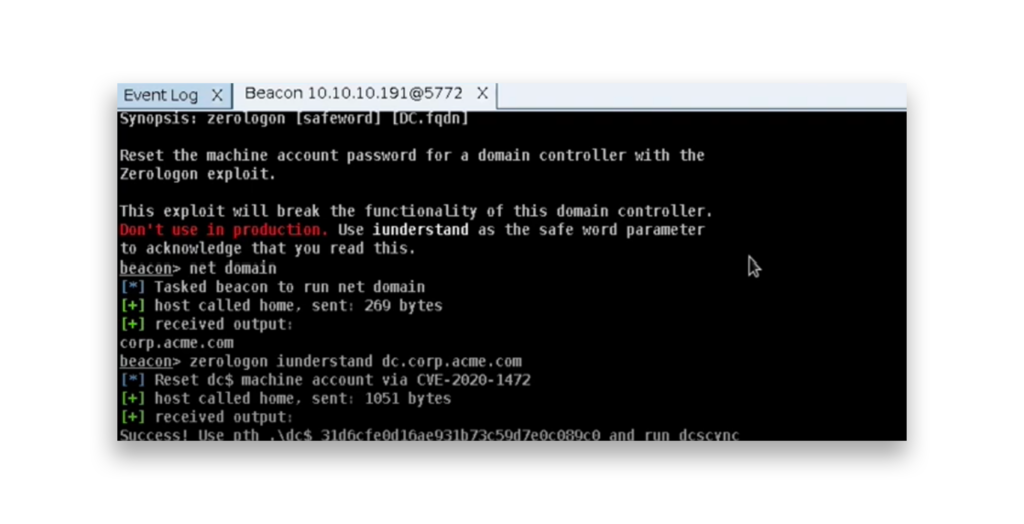
Figure 2 shows an example of a successful Zerologon attack in Cobalt Strike. The machine account password for the DC has been reset using Zerologon (CVE-2020-1472), and the output shows that the exploit worked. The attacker is then prompted to use the new password hash to run a DCSync attack and continue the exploitation.

How can you defend your environment from a Zerologon exploit?
Defenders can use Purple Knight to detect the presence of the Zerologon vulnerability (CVE-2020-1472) within their environment (Figure 3). This tool can help identify DCs that might be vulnerable. Administrators can then ensure that the appropriate security patches are applied. (You should always install the latest security patches on your DCs to ensure protection against evolving threats.)
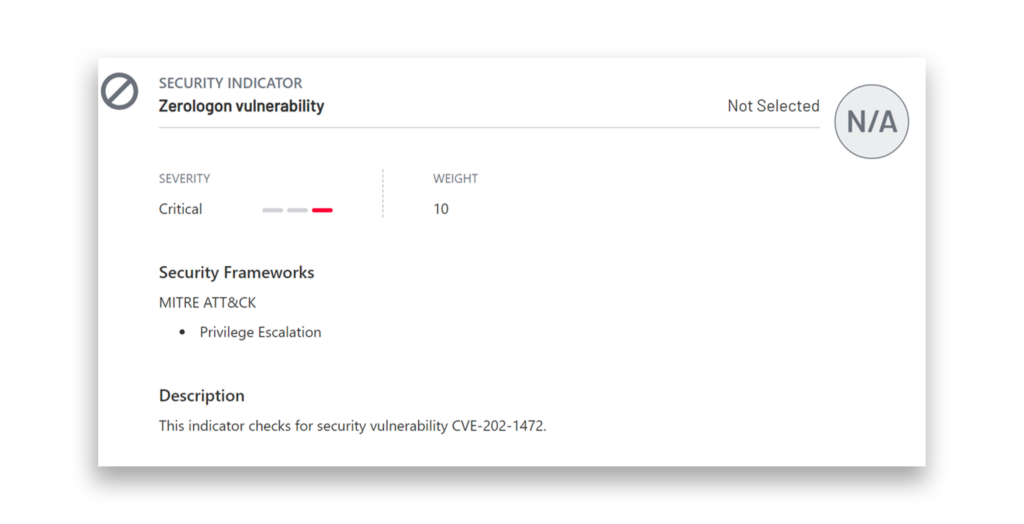
How can you detect a Zerologon exploit?
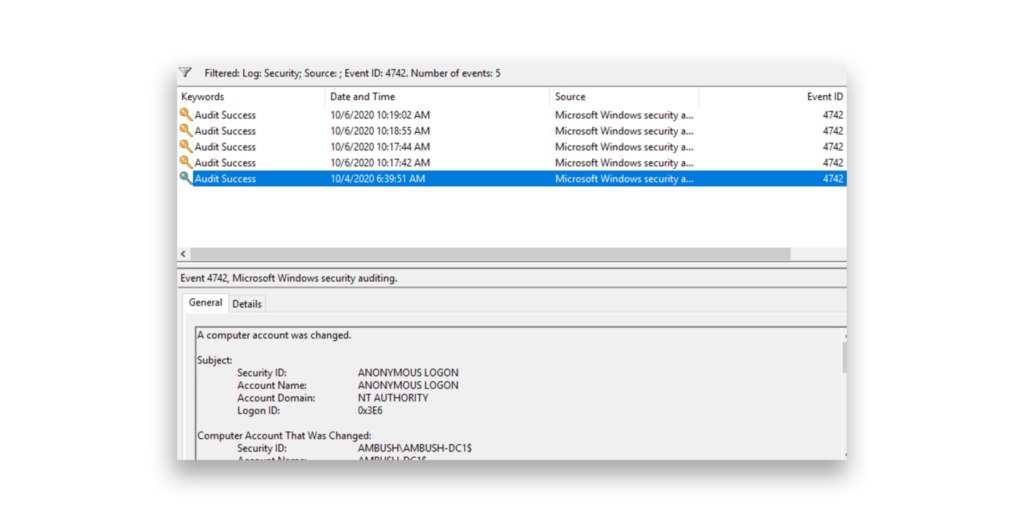
A primary sign of successful exploit is a computer account password reset. This type of reset appears in the security logs as Event ID 4742 (“A computer account was changed”), with the change being made by Anonymous Logon (Figure 4). If you see this event and confirm that the DCs haven’t been patched for the Zerologon vulnerability, it’s likely a true positive and a sign of active exploitation.
Threat actor profiles
The following threat actors have been known to exploit Zerologon in the wild.
- RansomHub2
- Black Basta (MITRE ATT&CK Software S1070)3
- Cuba (MITRE ATT&CK Software S0625)4
- Ryuk (MITRE ATT&CK Software S0446)5
Zerologon exploit tools
The following public tools and scripts, available on github.com, can be used to exploit the Zerologon vulnerabilty and have been observed in use during real-world incidents.
- gentilkiwi/mimikatz
- BC-SECURITY/Invoke-ZeroLogon
- leitosama/SharpZeroLogon
Threat overview
ATT&CK Tactic: Privilege Escalation
On September 20, 2024, Trend Micro highlighted how the RansomHub ransomware gang exploits the Zerologon vulnerability (CVE-2020-1472) to gain control of domain controllers without requiring authentication. This allows them to escalate privileges and take over the entire network, which allows them to deploy ransomware across the environment.6
On September 19, 2024, Qualys reported that the Black Basta ransomware gang uses the Zerologon vulnerability (CVE-2020-1472) as part of their attack strategy. By exploiting this flaw, they gain control over domain controllers. This gives them the access they need to spread ransomware across the network, steal data, encrypt systems, and so on.7
On August 17, 2023, BlackBerry reported that the Cuba ransomware gang leveraged the Zerologon vulnerability (CVE-2020-1472) as part of their attack strategy. By exploiting this flaw, they were able to reset passwords on domain controllers and gain elevated access to networks. This gave them control to deploy ransomware and steal data.8
On October 20, 2020, NetSec reported that the Ryuk ransomware gang leveraged the Zerologon vulnerability (CVE-2020-1472) to take over domain controllers and escalate privileges. By exploiting this flaw, they were able to reset domain controller passwords and achieve full network access. Ryuk used this technique to encrypt an entire domain in as little as five hours, moving rapidly to lock down critical systems and demand ransoms.9
Semperis snapshot
Zerologon (CVE-2020-1472) is a critical vulnerability in the Netlogon Remote Protocol that enables attackers to take full control of DCs, without authentication. By exploiting this flaw, attackers can reset passwords and gain domain-wide access, leading to significant security breaches.
Several ransomware groups, including Ryuk, have leveraged Zerologon to escalate privileges and encrypt entire networks in a matter of hours. Defenders can use Purple Knight to detect the Zerologon vulnerability within their environment, then take the necessary action to close this vulnerability. Applying patches and securing DCs are important steps in defending against this type of attack.
Additional resources
Endnotes
- https://frsecure.com/blog/cve-2020-1472/
- https://malpedia.caad.fkie.fraunhofer.de/actor/ransomhub
- https://attack.mitre.org/software/S1070/
- https://attack.mitre.org/software/S0625/
- https://attack.mitre.org/software/S0446/
- https://www.trendmicro.com/en_us/research/24/i/how-ransomhub-ransomware-uses-edrkillshifter-to-disable-edr-and-.html
- https://blog.qualys.com/vulnerabilities-threat-research/2024/09/19/black-basta-ransomware-what-you-need-to-know
- https://blogs.blackberry.com/en/2023/08/cuba-ransomware-deploys-new-tools-targets-critical-infrastructure-sector-in-the-usa-and-it-integrator-in-latin-america
- https://www.netsec.news/ryuk-ransomware-gang-uses-zerologon-exploit-to-achieve-domain-wide-encryption-in-just-5-hours/
The post Zerologon Exploit Explained appeared first on Semperis.
